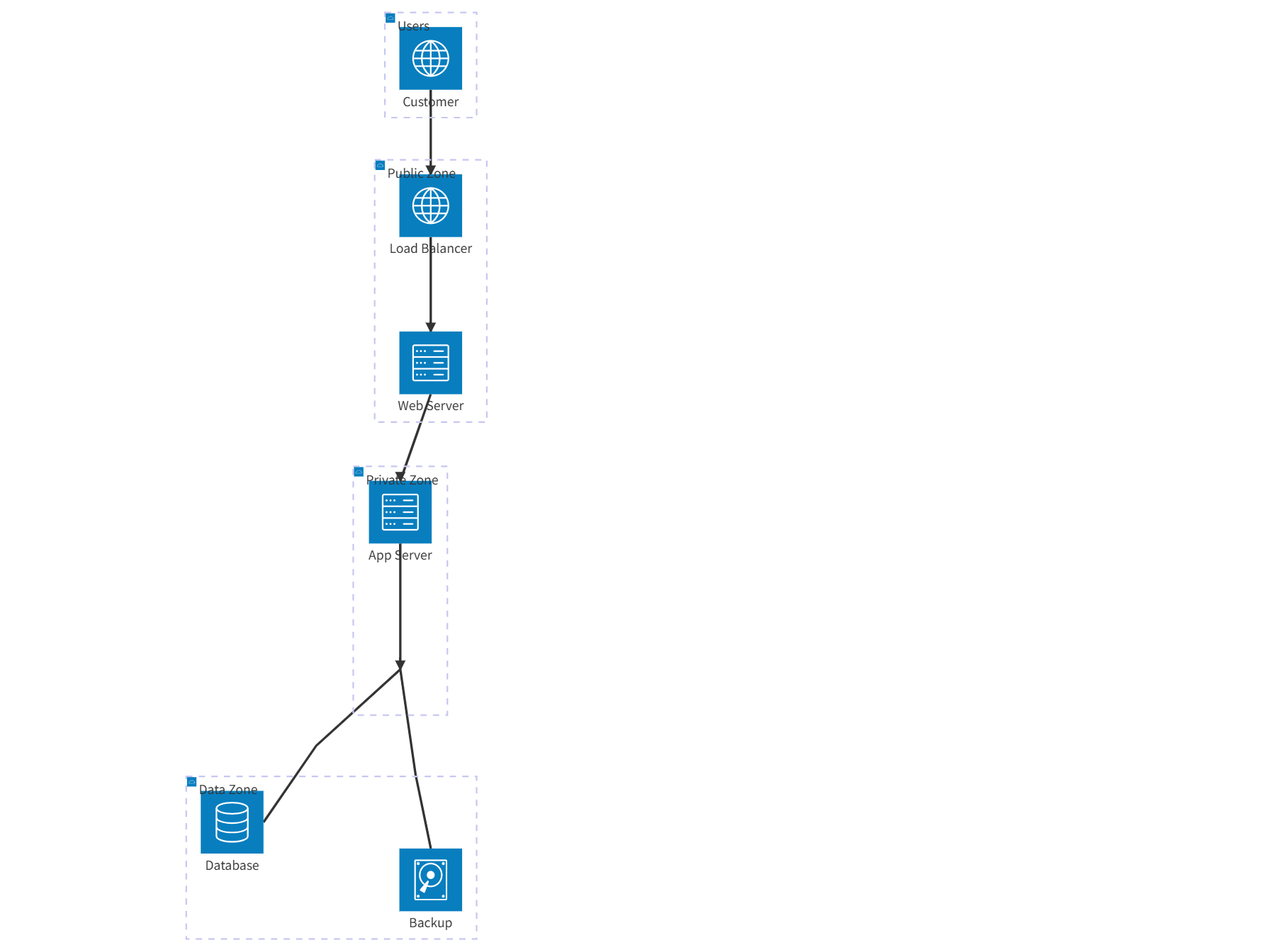
Added on:
May 07, 2025
User Prompt
Class Diagram for Web Application: Designing User Authentication and Authorization Mechanisms
Description
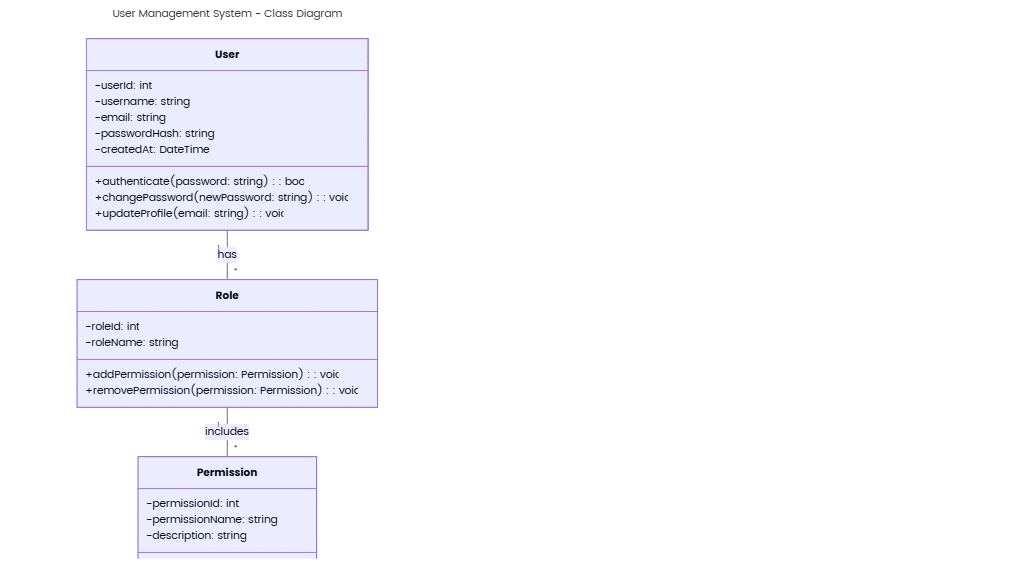
This class diagram models the core components of user authentication and authorization in a web application, emphasizing secure identity management and role-based access control (RBAC).
Core Classes & Attributes
- User
- Attributes: UserID (PK), Username, Email, HashedPassword, IsActive, LastLoginDate.
- Methods:
authenticate(String password),changePassword(). - Role: Represents individual users with unique credentials.
- Role
- Attributes: RoleID (PK), RoleName (e.g., "Admin", "Editor", "Guest"), Description.
- Associations:
- Many-to-Many with User: A user can have multiple roles (e.g., "Admin" + "Editor"), and a role can be assigned to multiple users.
- Permission
- Attributes: PermissionID (PK), PermissionName (e.g., "CreatePost", "DeleteUser"), Resource (e.g., "Article", "User").
- Associations:
- Many-to-Many with Role: A role (e.g., "Admin") inherits multiple permissions, and a permission can be granted to multiple roles.
- AuthenticationService
- Methods:
login(String username, String password),logout(),generateJWT(User). - Role: Manages session creation, JWT token generation, and integration with external auth providers (e.g., OAuth).
- Methods:
- AuthorizationFilter
- Methods:
validateToken(String jwt),checkPermission(String requiredPermission). - Role: Acts as a middleware to intercept requests, validate JWT tokens, and enforce permission checks before granting access to resources.
- Methods:
- OAuthProvider
- Subclasses:
GoogleOAuth,FacebookOAuth. - Methods:
redirectToLogin(),fetchUserProfile(String authCode). - Role: Implements third-party authentication flows, extending
AuthenticationService.
- Subclasses:
Key Relationships
- User ↔ Role: Many-to-Many via UserRole Association
- Intermediate class
UserRolerecords role assignments (e.g.,UserID=1assignedRoleID=2onDate=2024-01-01).
- Intermediate class
- Role ↔ Permission: Many-to-Many via RolePermission Association
- Intermediate class
RolePermissiondefines permissions for each role (e.g.,RoleID=2(Editor) grantedPermissionID=5(EditArticle)).
- Intermediate class
- AuthenticationService ↔ OAuthProvider: Inheritance
- Concrete OAuth classes inherit from
OAuthProvider, reusing common methods likeredirectToLogin().
- Concrete OAuth classes inherit from
- AuthorizationFilter ↔ User: Dependency
AuthorizationFilteraccessesUserandRoledata to validate permissions (e.g., checking if a user’s role includes "DeleteUser" permission).
Workflows & Business Logic
- Authentication Flow:
- User submits credentials via
LoginController, triggeringAuthenticationService.login(). - If credentials are valid,
AuthenticationServicegenerates a JWT token containing user roles/permissions and returns it to the client.
- User submits credentials via
- Authorization Flow:
- Client includes the JWT token in subsequent requests.
AuthorizationFilterintercepts requests, decodes the token, and usesRolePermissionmappings to check if the user has permission to access the requested resource (e.g.,/api/users/deleterequires "DeleteUser" permission).
- Role-Based Access Control (RBAC):
- Admins assign roles to users via the
UserRoleinterface, and roles are mapped to permissions viaRolePermission. - Example: A "Guest" role may have only "ReadArticle" permission, while an "Admin" role has "CreateUser", "DeleteUser", and "ManageRoles".
- Admins assign roles to users via the
- Third-Party Authentication:
- Users can log in via
GoogleOAuth, which callsfetchUserProfile()to retrieve email/roles from Google, creating or updating aUserrecord in the system.
- Users can log in via
Design Principles
- Security:
- Passwords are stored as hashes (never plaintext) in the
Userclass. - JWT tokens are short-lived and include refresh tokens for secure session management.
- Passwords are stored as hashes (never plaintext) in the
- Scalability:
- Separate
RoleandPermissionclasses allow granular permission updates without modifying user records. OAuthProvidercan be extended to support new auth providers (e.g., GitHub, Twitter).
- Separate
- Single Responsibility:
AuthenticationServicehandles login/logout,AuthorizationFiltermanages access control, andUserfocuses on profile data.