Added on:
May 07, 2025
User Prompt
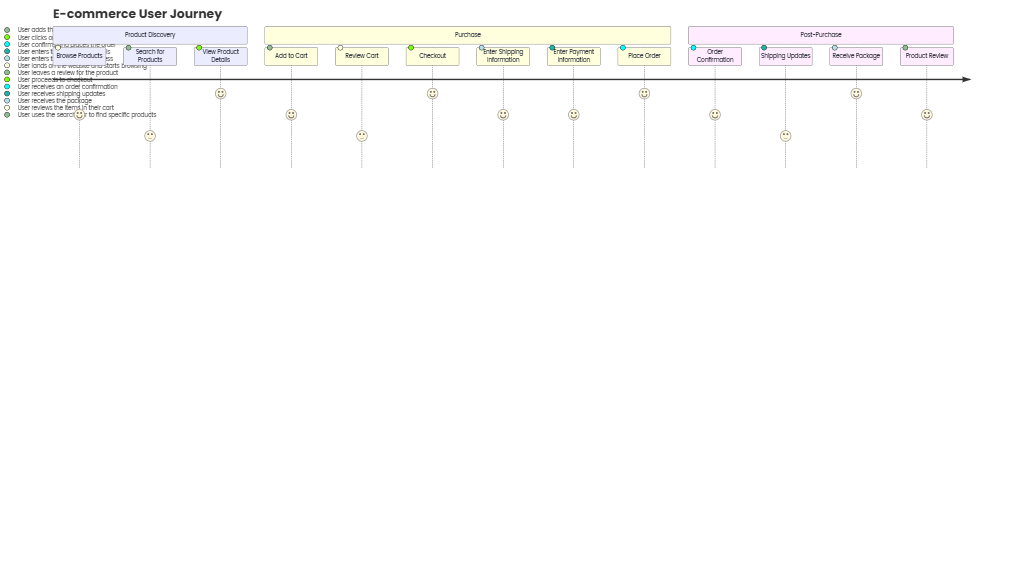
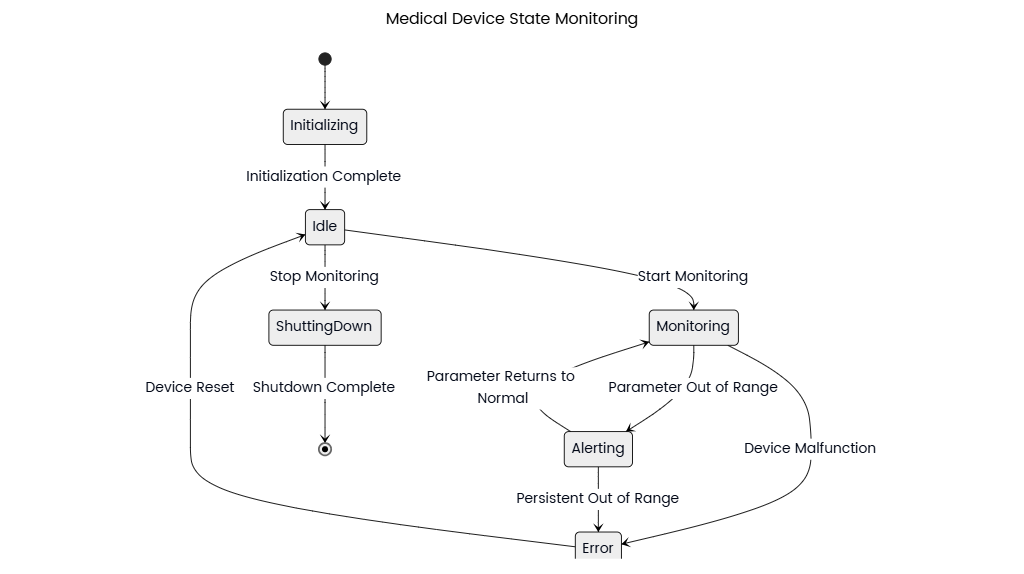
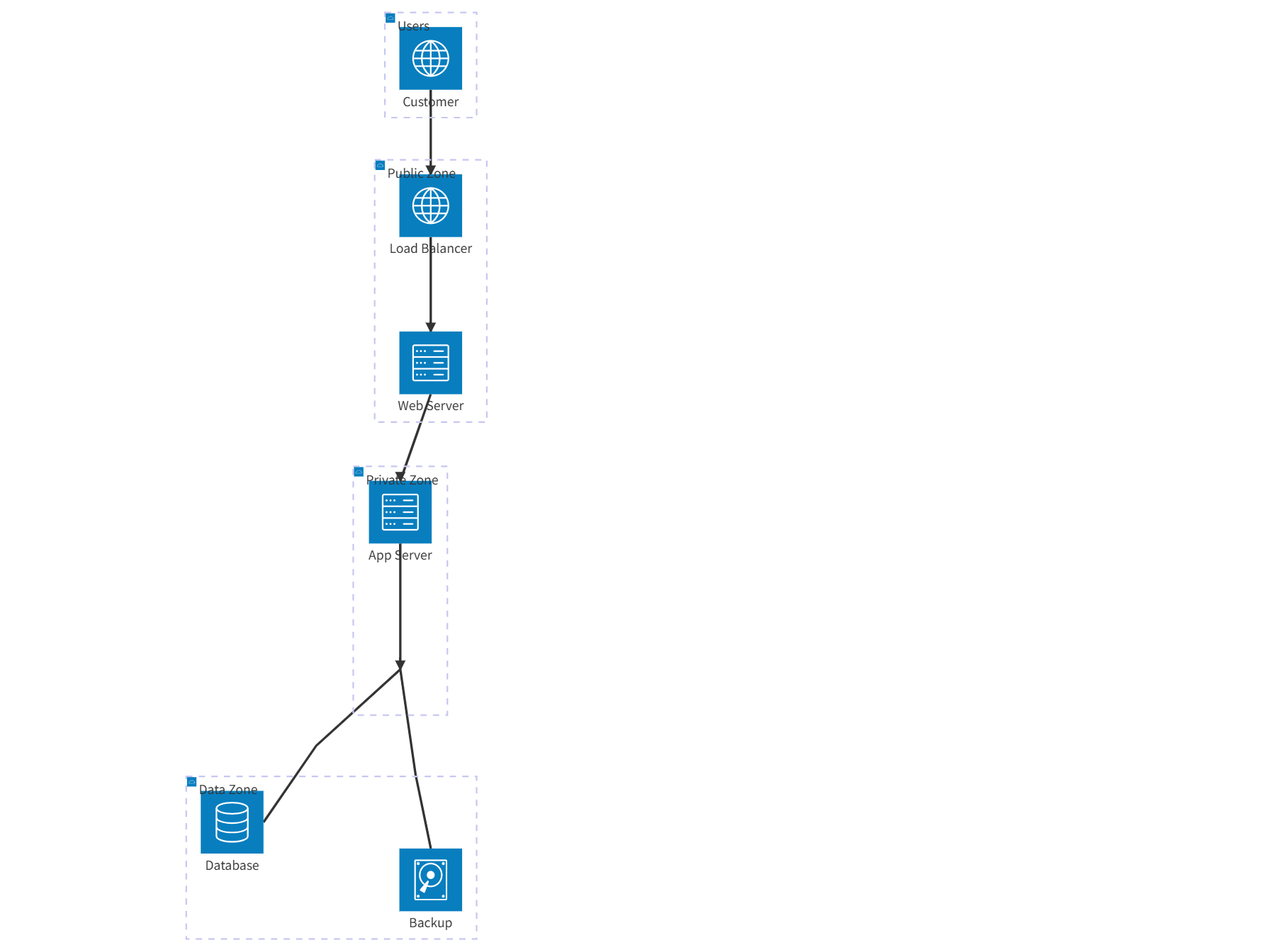
State Diagram for Web Application Session Management
Description
This state diagram models the lifecycle of a user session in a web application, illustrating key states, transitions, and events that manage user authentication, authorization, and session expiration.
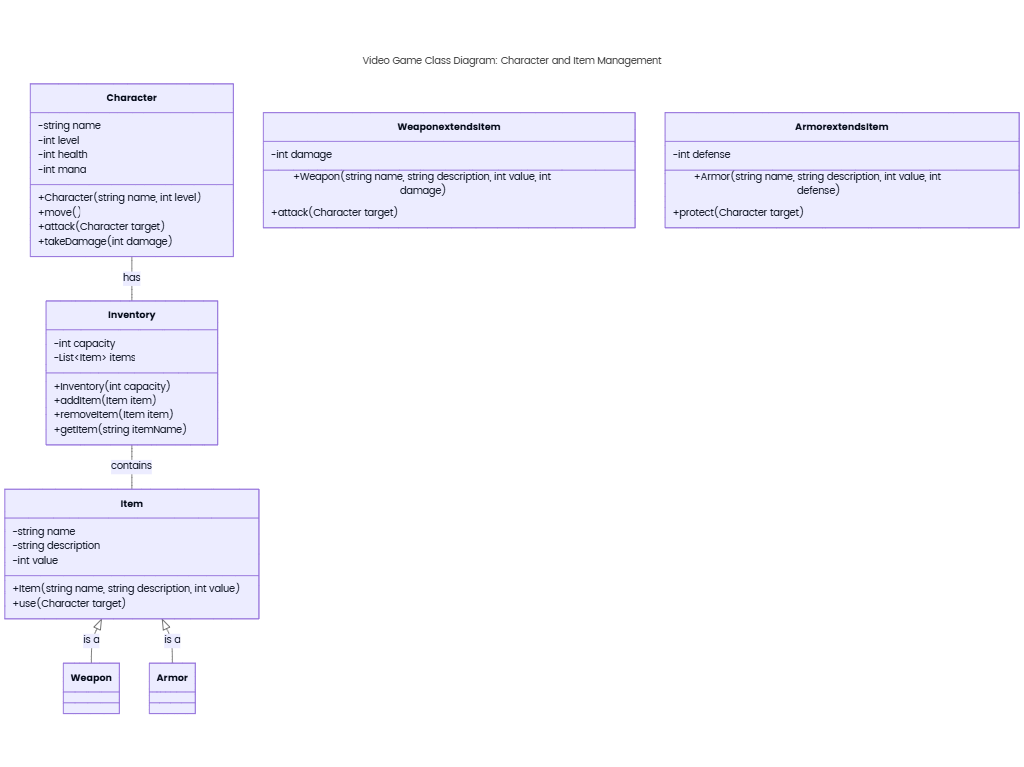
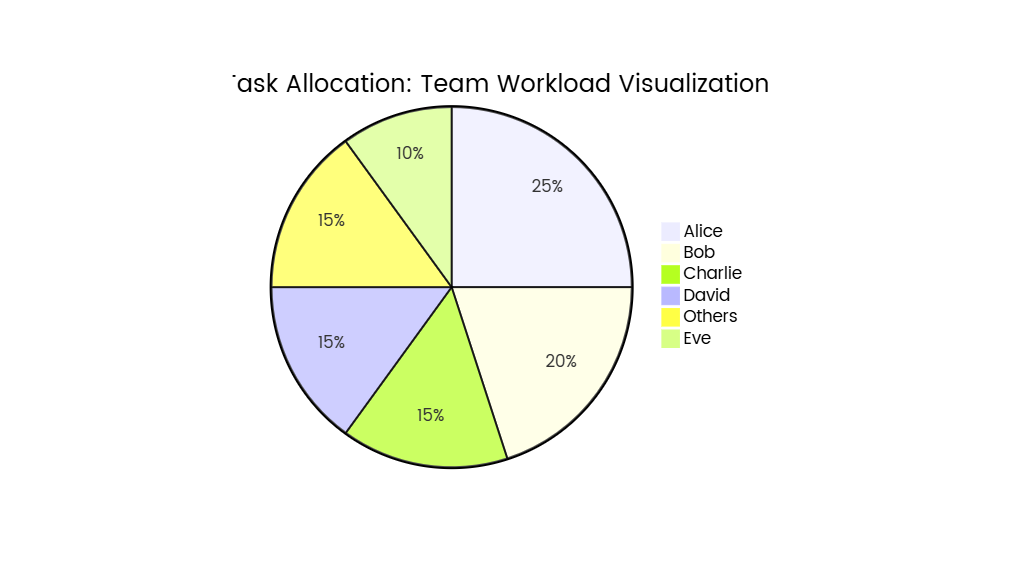
Core States
- Unauthenticated
- Description: User has not logged in; access is restricted to public routes (e.g., login page, homepage).
- Triggers:
- Initial page load.
- Session timeout or explicit logout.
- Authenticated
- Description: User successfully logs in; session is created with a unique ID (e.g., JWT token or session cookie).
- Triggers:
- Valid credentials submitted via login form.
- Successful OAuth/SSO verification.
- Active
- Description: User is actively interacting with protected routes (e.g., viewing dashboard, creating content).
- Triggers:
- Navigation to authenticated routes (e.g.,
/dashboard). - Periodic session refresh (e.g., token renewal every 30 minutes).
- Navigation to authenticated routes (e.g.,
- Idle
- Description: User is authenticated but inactive (no requests for a defined period, e.g., 15 minutes).
- Triggers:
- Inactivity timeout detected by client-side script or server middleware.
- Expired
- Description: Session has expired (e.g., token validity exceeded, idle timeout reached); access requires re-authentication.
- Triggers:
- Token expiration timestamp reached.
- Server-side session invalidation (e.g., admin revocation).
- Revoked
- Description: Session is forcefully terminated (e.g., password change, security breach).
- Triggers:
- User logs out explicitly.
- Security event (e.g., suspicious activity detected).
Key Transitions & Events
- Login Success
- Event: Valid credentials submitted.
- Transition: Unauthenticated → Authenticated → Active.
- Actions:
- Generate session token (JWT or cookie).
- Store user context (roles, permissions).
- User Activity
- Event: Request to protected route (e.g., API call).
- Transition: Active → Active (refreshes idle timer).
- Actions:
- Validate token signature.
- Check permission for requested resource.
- Inactivity Timeout
- Event: No requests for
Xminutes (e.g., 15 minutes). - Transition: Active → Idle.
- Actions:
- Client-side script triggers warning modal.
- Server may invalidate token on next request.
- Event: No requests for
- Token Refresh
- Event: Periodic refresh (e.g., every 30 minutes) or user activity during idle state.
- Transition: Idle → Active.
- Actions:
- Issue new token with updated expiration.
- Extend session lifespan.
- Explicit Logout
- Event: User clicks "Logout" button.
- Transition: Active/Idle → Revoked → Unauthenticated.
- Actions:
- Delete session token (client and server).
- Clear user context.
- Forced Invalidation
- Event: Password change, security policy update, or admin action.
- Transition: Active/Idle → Revoked.
- Actions:
- Invalidate all active tokens for the user.
- Notify user via email or UI alert.
Error Handling & Edge Cases
- Invalid Token:
- Transition: Any state → Unauthenticated.
- Trigger: Tampered token, expired signature, or revoked token.
- Action: Redirect to login with error message (e.g., "Session expired; please log in again").
- Concurrency Control:
- Transition: Active → Revoked.
- Trigger: Multiple logins detected; only the latest session is allowed.
- Action: Invalidate older tokens, notify user of concurrent access.
- Session Hijacking Detection:
- Transition: Active → Revoked.
- Trigger: Geolocation mismatch, unusual IP, or device change.
- Action: Force logout and trigger two-factor authentication (2FA) on next login.
Design Considerations
- Security:
- Use short-lived access tokens with refresh tokens for secure session renewal.
- Store tokens in HTTP-only cookies to prevent XSS attacks.
- User Experience:
- Gracefully handle idle timeouts with warnings (e.g., "Your session will expire in 2 minutes").
- Allow seamless token refresh without interrupting user workflow.
- Scalability:
- Centralize session management in a distributed cache (e.g., Redis) for multi-server deployments.
- Use asynchronous events (e.g., WebSockets) to push session invalidation across devices.